Introduction
The digital landscape is fast-changing and increasingly vulnerable to complex and persistent cyber threats. It requires more than the usual security defences, which often only react to threats and can be bypassed by attackers. To be ahead of the curve, an organization needs a more proactive and adaptive approach to cybersecurity. This is where deception technology comes into play.
What is Deception Technology?
Deception technology is a proactive cybersecurity approach based on decoys, traps, and fake appearances intended to divert the attackers away from critical systems and data. Traditional defences have aimed at keeping intruders out; in contrast, deception strategies begin with the premise of a breach. This technology confuses the attacker, slows them down, and provides valuable insights into methods by providing an environment full of convincing decoys, like fake credentials, data files, or even whole systems.
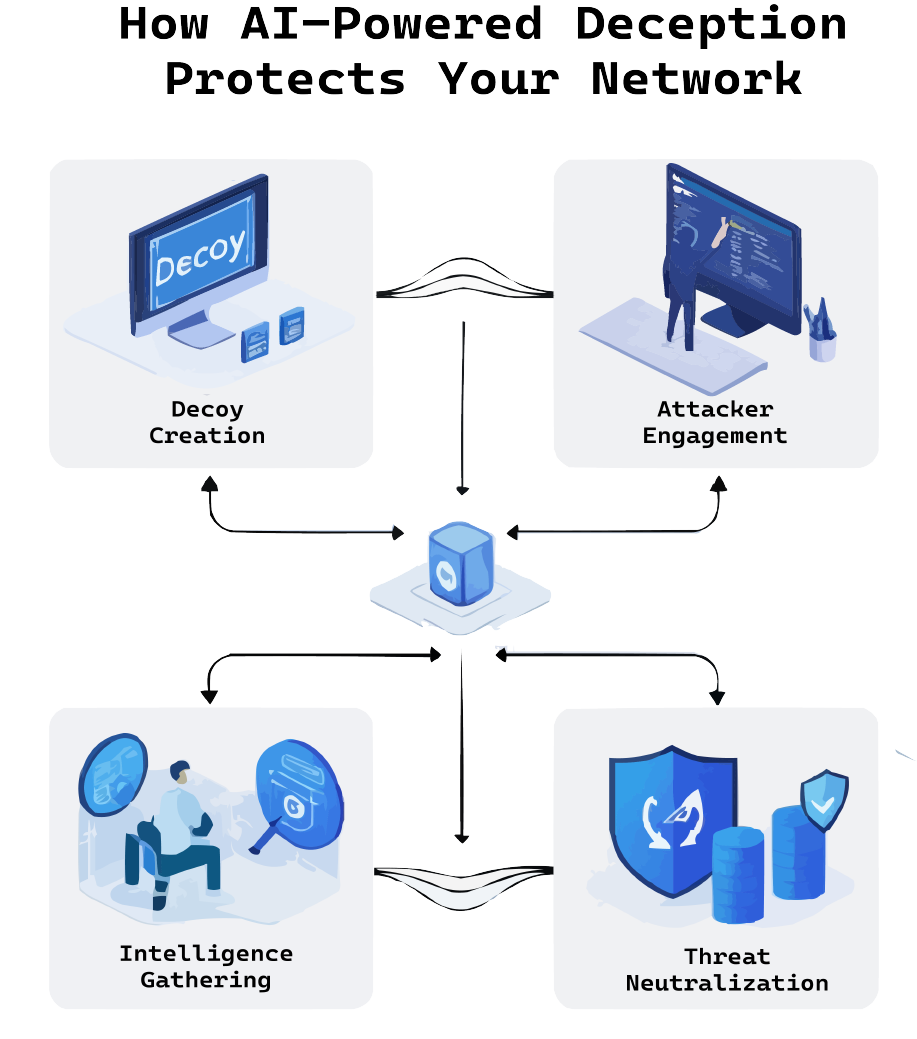
How Deception Technology Works?
Deployment of Decoys
Fake systems, servers, files and credentials are laid out where real assets would appear, enticing attackers to explore an environment that is at its core a trap.
Monitoring and Alerts
Responsive alerts to interactions by an attacker, with a decoy asset allow the security team to identify possible intrusions and pinpoint attacker’s IP address in real time.
Engagement and Analysis
The engagement provides security teams with real-time insights into attackers’ strategies, tools, and methods used during interactions with decoys. This data helps identify vulnerabilities, bolster defences, and anticipate future attack vectors.
Continuous Improvement
Insights from attacker’s methods are used to enhance the overall security posture of an organization, thereby improving defences against future threats.
Benefits of Deception Technology
Early Detection of Threats
Deception tools are designed to catch unauthorized activity in its very earliest stages. Once the attacker interacts with a decoy asset, an immediate alert is sent, signalling the presence of an attacker in the environment and a possible breach. It allows security teams to react more quickly and take action before the attack causes damage.
Real-Time Threat Intelligence
Instead of reacting after an attack has occurred, deception technologies can detect the attackers in their reconnaissance phase, hence enabling the shrinking of response time to the bare minimum. In addition, the interaction with decoys offers insight into Tactics, Techniques, and Procedures for toughening defences and gaining anticipation of future attacks. This real-time intelligence lets organizations adapt to the threats that lie in wait.
Extremely low False Positives
Unlike traditional systems, which are prone to generating many false alarms, deception technology generates high-fidelity alerts. Because the decoy assets are rarely touched by the legitimate user, any activity on the decoy assets is a strong indicator of malicious intent.
Enhanced Incident Response
With clear notifications and comprehensive data on the threats, it enables the security teams to respond in the best manner much more quickly. Such insights drive smarter decisions at a moment’s notice.
Integration with Other SOC Tools
Deception technology integrates with existing Security Operations Center (SOC) tools, such as SIEM systems, firewalls, or other layers of security. Through advanced threat detection response via actionable alerts to these systems, threat response is allowed, providing full visibility into an organization’s security posture.
Customization and Scalability
Deception technology can be tuned to replicate very specific IT environments, including financial or healthcare systems. It is highly adaptable and designed to scale as an organization grows from a small to large enterprise.
Cost-Effective Security
Compared to traditional cybersecurity tools, deception technology is less expensive and can easily be integrated into the system. This adds a robust layer of defence without much cost.
Deception as the Future of Cyber Defence
In the current threat landscape, traditional cybersecurity is just not sufficient. Advanced attackers easily bypass even the most advanced firewalls and endpoint protections. Deception Technology is a game-changer that flips traditional threat defence on its head: proactive engagement and disruption of threats rather than strictly defending. Proactively, it not only secures the most critical assets but also arms the organization with knowledge of attackers’ methods to counter future attacks.

Treacle’s iMirage Proactive Defence System uses cutting-edge AI together with Deception Technology to offer the most impeccable protection for IT/OT networks. To the attacker, it is a constantly changing environment; to the organization, it is early detection, collection of actionable intelligence, and response. In a continually changing cybersecurity world, Treacle’s iMirage Proactive Defence System offers a powerful way to stay ahead of the game.
Stay Ahead, Stay Secure!

Comments are closed