How SEBI’s Framework and AI-Powered Deception Technology Forge a New Path for CISOs
The rise of cyber threats in India’s financial landscape has pushed organizations to rethink their defenses. SEBI’s rethinking Cybersecurity and Cyber Resilience Framework (CSCRF) is a bold step in mandating advanced security practices for regulated entities. However, meeting these standards requires more than compliance—it demands a proactive defense strategy coupled with a clear understanding of how to tailor these measures to your organization’s unique risk profile.
For some, navigating these complexities might seem daunting, and this is where engaging a Virtual Chief Information Security Officer (vCISO) can provide invaluable clarity. A vCISO offers expertise to audit, analyze, and recommend strategies that not only ensure compliance but also align with broader security goals. This added layer of guidance can be pivotal for organizations seeking a comprehensive and efficient path forward.
At Treacle Tech, we specialize in AI-powered deception technology, a cutting-edge solution that doesn’t just react to threats but actively lures attackers into controlled traps, turning cyberattacks into actionable intelligence.
Cybersecurity’s Growing Complexity
India’s financial sector has become a prime target for sophisticated cyber adversaries. As networks grow complex and attackers deploy advanced tools, the reactive approaches of traditional security systems—such as firewalls and endpoint detection—often fail to keep up.
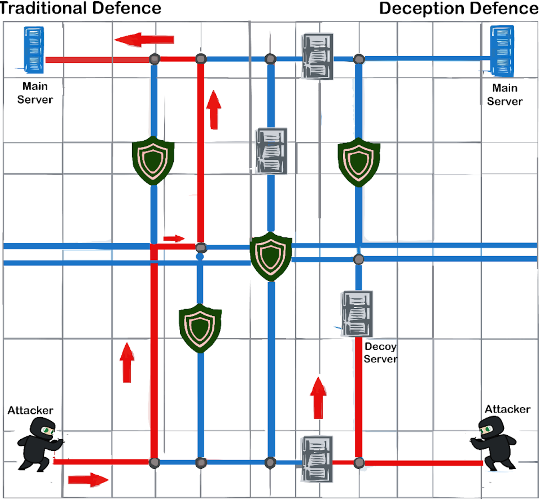
Consider the lessons of modern warfare: when military aircraft face heat-seeking missiles, they deploy flares to misdirect the missile. The missile chases the decoy, sparing the aircraft. In cybersecurity, deception technology works similarly, deploying fake assets like honeypots that attackers perceive as genuine.
This shift from detection to misdirection is the future of proactive cybersecurity.
SEBI’s Push for Cyber Resilience
SEBI’s CSCRF highlights the need for:
- Real-time threat monitoring
- Incident response readiness
- Adaptive cybersecurity measures
While compliance might seem challenging, it’s an opportunity to fortify defenses against a volatile threat landscape. Organizations now need solutions that meet regulatory expectations and future-proof their infrastructure.
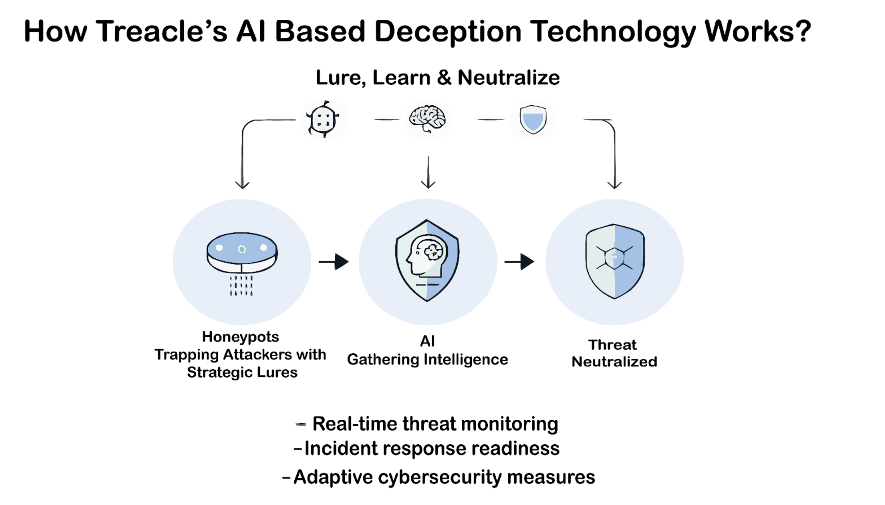
AI-Powered Deception: A Game-Changer for CISOs
Deception technology isn’t just a buzzword; it’s a transformative approach to threat management. Here’s how it works:
- Decoy Creation: AI-powered systems generate dynamic honeypots resembling critical assets.
- Engagement & Misdirection: Attackers are drawn to these decoys, believing they’ve breached real systems.
- Intelligence Gathering: While attackers interact with the fake environment, defenders gain real-time insights into their tactics.
- Neutralization: With actionable data, security teams can respond swiftly and neutralize threats.
Example: Imagine a cybercriminal targeting your payment processing system. Instead of accessing real servers, they infiltrate a deceptive environment tailored by Treacle Tech. As they proceed, our AI captures their movements, identifying vulnerabilities in their strategy—all while your real systems remain untouched.
Bridging Compliance and Innovation
For CISOs tasked with implementing SEBI’s guidelines, AI-powered deception technology offers unique advantages:
- Regulatory Compliance: Capturing and reporting attacker data aligns with SEBI’s incident-response mandates.
- Scalable Protection: Our dynamic solutions adapt to your network’s growth and evolving threats.
- Proactive Defense: Attackers are trapped in controlled zones, buying defenders time to respond.
The Road Ahead: Transforming Challenges into Opportunities
SEBI’s framework challenges organizations to evolve, but compliance shouldn’t be seen as a burden. It’s a chance to embrace proactive, AI-driven defenses that not only meet regulatory standards but also provide a strategic edge in an unpredictable threat landscape.
At Treacle Tech, we’re not just about compliance—we’re about innovation. Our AI-powered deception technology turns cyberattacks into intelligence, helping you stay resilient and agile.
Ready to Redefine Your Cybersecurity Strategy?
Book your free security audit today and discover how Treacle Tech can empower your organization with AI-powered deception technology. Let’s build the future of cybersecurity together.

Comments are closed